Cybersecurity: A discussion on the EU's NIS2 Directive with ABB's Global Cybersecurity Lead Tobias Nitzsche
Hydrocarbon Processing (HP) sat down with Tobias Nitzsche (TN), Global Cyber Security Practice Lead, ABB, to discuss the European Union’s (EU’s) NIS2 Directive—the EU-wide legislation on cybersecurity—and how it will affect the hydrocarbon processing industry.
HP: Can you provide an overview of the NIS2 Directive and its primary objectives? How does it differ from the original NIS Directive?
TN: The new NIS2 Directive strengthens security requirements, streamlines reporting rules, addresses supply chain security, and introduces stricter supervisory and enforcement measures. Importantly, NIS2 requires EU member states to adopt and enforce stricter cybersecurity regulations, across a broader range of entities and sectors. Unlike NIS1, which targeted critical infrastructure1, essential services and digital service providers, the updated rules apply to public and private sector organizations, including companies and suppliers that play a critical role in the economy and society by providing “essential” or “important” services, such as energy and water utilities, healthcare, food, manufacturers and chemicals.
HP: What are the key requirements and changes introduced by the NIS2 Directive that will impact the hydrocarbon processing industry?
TN: Chemicals were not part of the NIS1 regulation. The new directive is likely to impact the hydrocarbon supply chain, and here key industry changes depend on existing cybersecurity practices. The primary requirements can be found in Articles 21 and 23. In a cyber-mature company, most of these requirements might be already addressed, especially in enterprise IT (information technology) but often not in OT (operational technology), and this is where I see the biggest gaps; you cannot just apply rules and mitigations in the same way you apply it to IT. Dedicated OT security teams need to drive it together with their IT security colleagues. Risks are different and require different treatments.
Another challenge will be the reporting obligations. Many industries are not ready for incident detection and handling in OT, which is the basis for timely reporting capabilities. Early warning needs to happen without delay and within 24 hrs after learning of incidents that could have significant impact. This poses a major challenge if there is no alignment or a misalignment between people, process and technology.
As most oil and gas companies were already regulated by NIS1, they could be aware and prepared, but now with NIS2, there is also a focus on the supply chain. I would expect to see the greatest impact here. Vendor audits and externally proven cybersecurity certificates will become more relevant. In addition to new heavy fines, NIS2 non-compliance can also lead to legal ramifications for management teams. It is vital that cybersecurity becomes a management board topic.
HP: What specific challenges do you anticipate for oil and gas companies in complying with NIS2?
TN: As mentioned before, the strict reporting obligations require huge efforts in identifying the best ways to prevent, detect (monitoring), report and respond when it comes to industrial environments, but also some of the risk management measures mentioned in Article 21 will become challenging, as we still often see outdated components and systems. These might not have the adequate capabilities to be secured and monitored. Here, manufacturers can help with SLAs (service level agreements), upgrades, consolidations or specific cybersecurity solutions for these systems.
HP: How should these companies prepare for the implementation of NIS2? What steps should they take immediately?
TN: Start with a risk analysis performed by OT experts (dedicated for OT environments—e.g., the IEC 62443 risk assessment approach). Based on the outcome, plan your cybersecurity program for mitigation—existing risk reduction roadmaps from vendors can be a good starting point. Another key aspect is to perform a business impact analysis taking cyber incidents into account; existing HAZOP/LOPA (hazard and operability study/layers of protection analysis) studies and analysis can be very useful for this exercise. This will help to create a needed incident response and disaster recovery plan, and thus defines needed SLAs, redundancies and backup and recovery systems, which are your last line of defense in a (cyber) disaster.
HP: How can an organization like yours support companies with compliance?
TN: Our organization is OT. We actively write industrial security standards together with other colleagues in the industry, which can then be applied by others in their risk assessments. Therefore, we know how to instinctively perform an OT-relevant risk assessment not only for our systems, as this is a standardized approach which should be the basis for implementing an information security management system. Furthermore, this helps to create a cybersecurity program for risk mitigation to an accepted level based on risk appetite and regulation needs. It will also be the basis for continuous monitoring and documentation of effectiveness, and finally compliance. In all these phases, we can advise our customers on their risk reduction roadmap along their cybersecurity journey.
HP: How does NIS2 address the cybersecurity risks associated with the increasing digitization and automation across industry, particularly oil and gas?
TN: I personally see digitization as a key element that will help centralize and automate not only process information and decisions but also security relevant information and handling, which will help identify bad actors in a more efficient and automated manner, hence much faster. NIS2 mandates that any digitization approach should include security functions in the design phase—this is complemented by the EU Cyber Resilience act.
HP: What are the best practices for integrating NIS2 compliance into existing cybersecurity frameworks?
TN: Even here, the standard itself provides some guidance. Article 25 says “to promote the convergent implementation of Article 21(1) and (2), Member States shall, without imposing or discriminating in favor of the use of a particular type of technology, encourage the use of European and international standards and technical specifications relevant to the security of network and information systems.” So, it is wise to follow existing standards like ISO 27000 Series and IEC 62443, which might already be the basis for existing cybersecurity frameworks.
HP: Looking ahead, how do you see NIS2 influencing the future of cybersecurity in the oil and gas sector? Is the risk landscape changing?
TN: NIS2 will influence the future of cybersecurity especially in the EU—e.g., with centralizing mandates and strengthening ENISA (European Union Agency for Cybersecurity). It will promote the establishment of a central register of digital infrastructure entities and digital service providers. Cybersecurity information-sharing arrangements will be encouraged within communities of essential and important entities, including relevant suppliers and service providers. EU-CyCLONe (cyber crisis liaison organization network) will involve representatives of Member States’ cyber crisis management authorities in cases of significant cyber incidents impacting services within the scope of this Directive.2 This will definitely influence the future of cybersecurity in the EU and not just only in the oil and gas sector. For the threat landscape, which will influence the risk landscape, ENISA is a good source. Their latest report was published their latest report in 2023 (ENISA Threat Landscape 2023). Over the past few years, the prime threats have not changed significantly (FIG. 1).
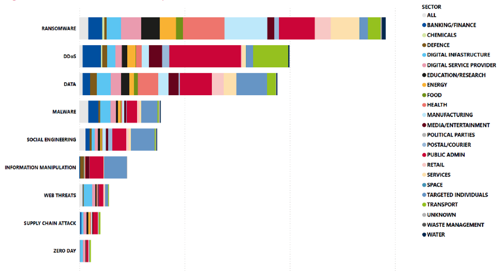
FIG. 1. Observed events related to prime ENISA threat level (ETL) threats in terms of affected sector. Source: ENISA.3
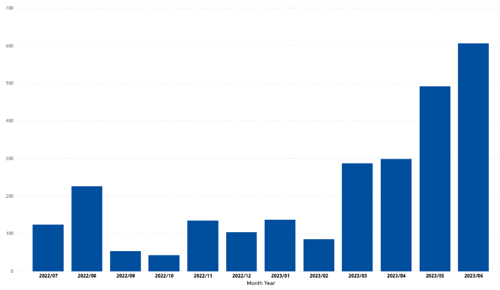
However, the timeline of EU events and observed incidents per month is growing and concerning (FIG. 2).
LITERATURE CITED
1 IT Governance, “The NIS Directive and NIS regulations”, online: https://www.itgovernance.co.uk/nis-directive
2 ENISA, “EU CyCLONe,” online: https://www.enisa.europa.eu/topics/incident-response/cyclone
3 ENISA, ENISA Threat Landscape 2023, October 19, 2023, online: https://www.enisa.europa.eu/publications/enisa-threat-landscape-2023?v2=1






Comments